 Submitted by skyred on
Submitted by skyred on
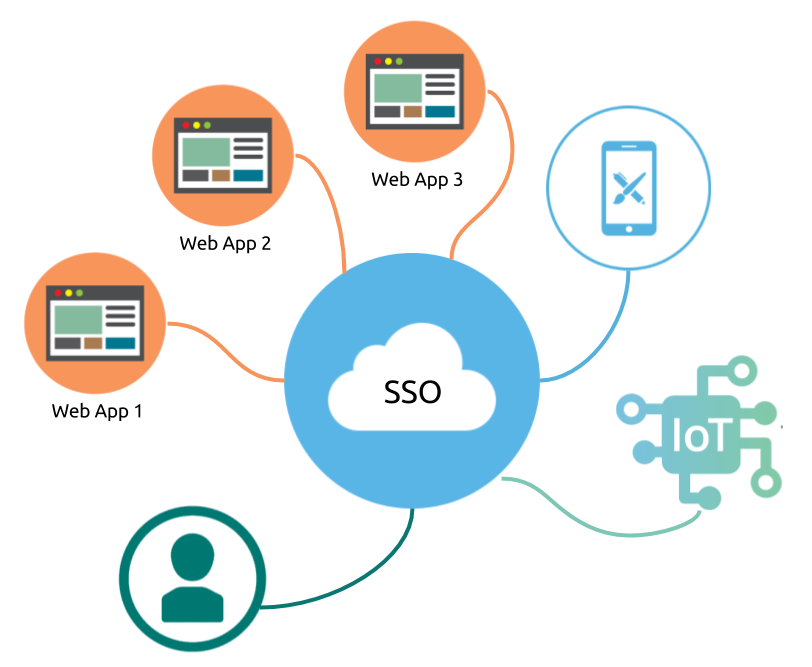
Single sign-on (SSO) is a property, where a user logs in with a single ID and password to gain access to a connected system or systems without using different usernames or passwords, or in some configurations seamlessly sign on at each system. A simple version of single sign-on can be achieved over IP networks using cookies but only if the sites share a common DNS parent domain. ---- https://en.wikipedia.org/wiki/Single_sign-on
As the definition suggests, one can imagine that SSO becomes one critical part of the system design and user experience design for complex and distributed system, or for a new application to integrate with the existing connected system. With SSO enabled, a system owner can manage access control at a centralized place, therefore granting users permissions cross multiple subsystem is organized. On the other hand, as an end user, he/she only needs to secure one set of credentials to access multiple resources or to access functionalities whose distributed architecture is hidden from the user.
As we entering 2018, our software becomes more complex and its services become more ubiquitous. Let's use Google's SSO for example to illustrate the demand for a modern SSO:
- A user can sign in with password once for both Gmail.com and YouTube.com
- A user can go to Feedly.com or New York Times and use the "Sign-in with Google" to authorize third parties to access the user's data
- A user can sign in with password on a mobile device to sync all photos or contacts from Google
- A Google Home device can connect to multiple people's Google accounts, and read out their calendar events when needed
- YouTube.com developers can use Polymer as frontend technology, and authenticate with YouTube.com backend to load the content via web services API
You might not realize the complexity of such system to support the modern use cases above until your system needs one, and you need to develop the support. Let's translate the above use cases into SSO technical requirements:
- Support SSO cross multiple domains
- Support Password Grant (sing-in directly on the web), Authorization Code Grant (user authorizes third-party), Client Credentials Grant (Machine sign-in), and Implicit Grant (third-party web app sign-in)
- Support distributed architecture, where your authentication server is not necessary on the same domain or at the same server as your resource servers
- Web services API on resources server can effectively authenticate requests
- No technology lock-in for authentication server, resource servers as well as client-side apps.
- Support a seamless user authorization experience cross different client-side technology (Web, Mobile or IoT), and cross different first-party and third-party applications
Fortunately, we can leverage existing open standards and open source software to implement a SSO for a distributed system. First, we will rely on OAuth 2.0 Authorization Framework and JSON Web Token (JWT) open protocols. OAuth 2.0 is used to support common authentication workflows; in fact, the above 4 types of grants in the requirements are the terminologies borrowed from OAuth 2.0 protocol. JWT protocol is used to standardize the sharing of a successful authentication result cross clients apps and resources servers. The protocol allows resources server to trust a client request without double checking with authentication server, which lowers the amount of communication within a distributed system, therefore increases the performance of overall authentication and identification. For more technical details on how to use OAuth 2.0 and JWT for authentication, please see Stateless authentication with OAuth 2 and JWT - JavaZone 2015.
Regarding to building the authentication sever, where all users and machines will sign-in, authenticate, authorize, or identify themselves, the critical requirement for the authentication server is that this server implements OAuth 2.0 protocol and use JWT as the bearer token. As long as the authentication server implements the protocols, the rest of facilitating features can be built on any technology. I like use simple_oauth module with Drupal 8, because out-of-box, this solution is the whole application, including users, consumers and tokens management. Particularly, I have been helping to optimize the user experience of user authorization process for different use cases. If you are not familiar with Drupal, a particular distribution Contenta CMS has pre-packaged simple_oauth and its dependencies for you.
Once the authentication server is in place, we will implement the protocol and workflows on resource server and client-side apps. This part is largely up to your resource server and client-side technologies you picked. We are building this part of integration with Node.js, Laraval, Drupal 7 and Drupal 8 applications. As the time of writing, we have published the module oauth2_jwt_sso on Drupal 8.
I leave the extensibility, limitation, and more technical details of this SSO solution for the upcoming DrupalCon Nashville session. I will include the session video here in late Apri, 2018.



Comments
btopro replied on Permalink
Fantastic post, roadmap on D7 and Node.js jwt modules?
This is exactly what I've been looking for using ContentaCMS as the authentication broker for a swarm of D7 / node.js docker containers. I've been looking to replace Bakery with something more standards based and the roads keep leading here; Any roadmap / modules out there for the node or D7 editions of this module?
Thank you for your interest!
For the authentication server, simple_oauth is only available on D8, and I haven't heard from @e0ipso that he would support D7. For resource server implementation, we are porting oauth2_jwt_sso,
module to D7, but I do not have an estimate yet. We also have an implementation in work for Node.js integration. Hopefully, we can publish them in the near future.
Add new comment